|
|
|
| Tried-and-True Tactics
Continue to Dominate |
| |
| Threat researchers are
always analyzing and predicting novel attacks. Now AI, Quantum Computers and
Vibe Coding are evolving the tried and true hacking
techniques. Resulting in a quicker and more efficient threat
to your data. Especially if it's cloud based. It's available
for anyone to attempt the attack. |
|
|
|
History of the Number of Attacks
1989 to 2025
1985 to 1995
1995
-
An estimate for
the U.S. Department of Defense (DoD) in 1995: about
250,000
unauthorized attempts to penetrate its
systems, with an estimated “65% successful” rate
noted for those attempts.
NIST Computer Security Resource Center+2Government
Accountability Office+2
-
A historical
review notes that in 1995 the first major bank hack
(by Vladimir Levin) moved over US$ 10 million from
Citibank accounts globally, indicating a successful
financially-motivated attack.
Arctic Wolf+1
1996
-
According to a
table of incidents reported by CERT Coordination
Center (CERT/CC) in the U.S., there were
2,573
incidents reported in 1996.
INL Digital Library+2ITU+2
-
One estimate from
a U.S. defence-document states that for U.S.
Department of Defense (DoD) networks, there were
about
500,000 “hacker attacks” in 1996, with a
stated “success rate” of ~65%.
NIST Computer Security Resource Center
-
It is also
documented that on 6 September 1996, a widespread
SYN-flood DDoS attack hit ISP Panix in New York —
one of the earliest public examples of such a
denial-of-service attack.
1997
-
For the U.S., the
Federal Bureau of Investigation (FBI) reported
408 cyber
intrusion investigations in 1997 — a
significant increase over 1996.
CISA+2ERIC+2
-
A survey of U.S.
organisations found that in 1997
64% of
respondents said their systems had been breached
multiple times, and the proportion of
organisations reporting an Internet-based intrusion
rose from 17% in 1996 to 54% in 1997.
RadioFreeEurope/RadioLiberty
-
The database of
incident reports to CERT Coordination Center
(CERT/CC) lists
2,134
reported incidents in 1997 (U.S. data).
1998
-
A U.S.-based
dataset shows that for the year 1998 there were
3,734
reported cyber-incidents (to the CERT/CC)
in the U.S. alone.
INL Digital Library+1
-
A survey by the
Computer Security Institute in cooperation with the
Federal Bureau of Investigation (FBI) found that
64% of U.S.
organizations surveyed had experienced a
security breach in the prior 12 months.
WIRED+1
-
It was also
reported that in 1998 the FBI opened
547
“computer intrusion” cases in the U.S
1999
-
The CERT
Coordination Center (CERT/CC) reported
9,859
incidents detected/reported in the U.S. in
1999.
inldigitallibrary.inl.gov+1
-
From the Computer
Security Institute/Federal Bureau of Investigation
(CSI/FBI) survey of U.S. organisations in 1999:
-
The Federal
Bureau of Investigation (FBI) investigated
1,756
computer intrusions (pending/opened) in FY
1999
2000
-
The worm ILOVEYOU
(also called “Love Bug”) spread rapidly in May 2000,
infecting millions of computers and causing major
disruptions.
Wikipedia+2Wikipedia+2
-
The teenager
“Mafiaboy” launched a large-scale denial-of-service
attack in early February 2000 against major websites
such as Yahoo!, Amazon and eBay.
WIRED+1
-
According to the
U.S.-based CERT Coordination Center, the number of
reported incidents for 2000 in the U.S. was
approximately
21,756.
GovTech
-
Reports indicate
that attacks on servers
doubled
in 2001 compared to 2000, implying significant
growth in incident volume around 2000.
2001
-
The CERT
Coordination Center (CERT/CC) recorded
52,658
security incidents in 2001 in the U.S., up
from ~21,756 in 2000.
WIRED+2OECD+2
-
A working paper
from the World Bank notes that about
70 % of
organizations in the U.S. in 2001 reported
serious security breaches (thefts of proprietary
information, denial-of-service, etc.), up from ~60 %
in 2000.
World Bank+1
-
An OECD-style
annex says that the number of “cyber-incidents
notified to CERT” had risen to “over 52,000 in
2001,” but are estimated to represent only about
one-fifth
of the actual occurrences.
2002
-
According to the
Computer Emergency Response Team Coordination Center
(CERT/CC) in the U.S., there were
≈ 82,094
security incidents reported for the year
2002.
Government Accountability Office+2CdrInfo+2
-
In the U.S., the
Computer Security Institute (CSI) together with the
Federal Bureau of Investigation (FBI) surveyed 503
organisations in 2002:
-
A U.S. report
noted that through the first 9 months of 2002 to
CERT/CC there were 73,359 incidents reported.
2003
-
The CERT
Coordination Center (CERT/CC) reported handling
137,529
computer security incidents in 2003
(January‑December) in the U.S. context.
SEI+1
-
It was noted that
for only the
first half of 2003, 76,404 incidents had been
reported to CERT/CC.
Government Accountability Office+1
-
The year saw
major worm outbreaks, for example the SQL Slammer
worm rapidly spreading in January 2003.
2004
-
According to the
International Monetary Fund (IMF) report, a chart
shows the “Number of cyber incidents” starting
around 2004, indicating several thousand incidents
in that year—but the exact figure is not clearly
published.
IMF
-
A report from
Symantec (a cybersecurity vendor) noted that in the
first half of 2004 there were
1,237 new
software vulnerabilities and “almost 5,000
new Windows viruses and worms” released.
WIRED
-
For phishing
specifically: between May 2004 and May 2005 in the
U.S., approximately
1.2 million
users suffered phishing‑related losses.
2005
-
A report by the
Bureau of Justice Statistics (BJS) on cyber crime
against U.S. businesses found that in 2005: among
~7,818 businesses surveyed, 3,247 reported monetary
losses from cyber‑incidents, totaling
US$ 867 million.
Bureau of Justice Statistics+1
-
The same report
indicates: ‘cyber attacks’ (a category which
includes malicious code/viruses, denial of service,
vandalism/sabotage) accounted for about
1,582,913
incidents in 2005 among responding firms.
Bureau of Justice Statistics+2Bureau
of Justice Statistics+2
-
Among U.S.
businesses responding to the National Computer
Security Survey: 67% detected some form of
cyber‑crime in 2005; about 60% detected one or more
“cyber attacks”.
Office of Justice Programs+1
-
Measurement of
denial‑of‑service (DoS) attacks: data from CAIDA
(Center for Applied Internet Data Analysis) show
that in 2005 they observed
over
68,000 DoS attacks directed at over 34,000
distinct victim IP addresses.
2006
-
The
FBI’s Internet Crime Complaint Center (IC3) received
207,492
complaint submissions during 2006 (covering
fraudulent and non‑fraudulent Internet‑related
incidents) and referred
86,279
of those for further investigation.
archives.fbi.gov
-
In 2006, security
analysts noted that zero‑day attacks (exploits of
previously unknown software flaws) “became a top
concern” and very targeted attacks exploiting
unpatched vulnerabilities proliferated.
CIO
-
A timeline of
“significant cyber incidents” (those involving
government agencies, defense, high‑tech companies or
financial crimes) begins in 2006, highlighting that
that year marked the start of more visible,
large‑scale attacks.
2007
-
A survey found
that 84.7%
of respondents (organizations) said their
organization was affected by a
successful
cyber‑attack.
Comparitech
-
A major incident
in 2007 was the 2007 cyberattacks on Estonia: a
large‑scale series of distributed‑denial‑of‑service
attacks against Estonian government, financial,
media and infrastructure systems.
Wikipedia
-
One threat report
noted that in 2006 (the year before) the U.S. hosted
more than one‑third of websites containing malicious
code; implying that the threat landscape in 2007 was
significant and growing.
2008
-
According to the
Kaspersky Lab Security Bulletin, in 2008 there were
23,508,073
attacks that originated from Internet
resources in 126 countries.
Securelist
-
In the same
report: computers in
215
countries were attacked (totaling
~23,680,646 attack‑events) in 2008.
Securelist
-
As a well‑known
incident: in 2008 the United States Department of
Defense (DoD) suffered a major malware infection
(USB‑stick “insider propagation”) often cited as one
of the worst breaches in U.S. military history.
Wikipedia
2009
-
According to
Symantec,
75 % of enterprises surveyed experienced
some form of cyber attack in 2009.
SecurityWeek+2Internet
News+2
-
The same Symantec
data indicated that
36 %
of those attacks were rated “somewhat” or “highly
effective” by the victims.
Internet News+1
-
Malware activity
boomed in 2009: for example, the anti‑virus vendor
PandaLabs reported that nearly
55,000 new
malware samples were discovered
each day in
2009.
Infosecurity Magazine
-
The vendor
Kaspersky recorded ~73.6 million
attacks (network/IDS events) for 2009, with
86% of those targeting just the top 20 countries.
Securelist
-
One study found
that data breaches caused by
malicious
attacks and botnets doubled from
12 % in
2008 to
24 % in
2009 among the organisations studied.
2010
-
The security firm
Kaspersky Lab reported that they recorded
≈ 580,371,937 web‑based attacks in 2010,
spanning 201 countries.
Securelist
-
A survey of
Canadian organizations found that cyber attacks
increased by about
29 %
in 2010 compared to the previous year.
SC Media
-
According to the
NortonLifeLock (formerly Norton) “Cybercrime”
report: ~431 million adults in 24 countries were
victims of some type of cyber‑crime in the past year
(the report released in 2011, covering 2010). Total
global losses were estimated at
US $388 billion for 2010.
securitymagazine.com
-
The number of
newly documented software vulnerabilities rose in
2010: over
8,000 new vulnerabilities recorded, a ~27 %
increase over 2009.
2011
-
According to
Verizon’s 2012
Data Breach Investigations Report, there were
855 data
breach incidents reported in 2011,
involving a total of
174 million
compromised records.
GovTech+1
-
According to
Symantec’s annual threat report: more than
5.5 billion
malicious attacks were blocked globally in
2011 — representing an increase of around
81 %
compared to the previous year.
GovTech
-
According to
Kaspersky Lab, in 2011 web‑based attacks reached
946,393,693
globally.
Securelist+1
-
Dos/DDD‑style
attacks: For the second half of 2011, some major
DDoS attacks were recorded, with very large scopes
and long durations.
2012
-
A report from the
Open Security Foundation / Risk Based Security found
that data‑breach incidents more than doubled to
2,644
incidents in 2012.
Tech Monitor
-
According to the
Ponemon Institute and Symantec Corporation, the
average cost per breached record globally rose in
2012 (to ~US$136 per record) and the number of
records compromised in the companies surveyed
increased.
Canadian Underwriter
-
The
PricewaterhouseCoopers (PwC) 2012 technical survey
found that
93% of large organisations and
76% of small
businesses reported that they were breached
in the past year.
PwC
-
In terms of
breach investigations, a summary of ~450 global data
breach investigations noted that in 2012 nearly
every
industry, country and type of data was involved.
Help Net Security
-
From the
Verizon Communications 2012 Data Breach
Investigations Report: they reported
855
data‑breach incidents involving
174
million compromised records (for data drawn
from 2011, but the report is marked 2012) .
2013
-
According to the
Symantec Corporation
Internet
Security Threat Report (Volume 19):
-
The number of
data breaches in 2013 increased by ~62 %
compared to the previous year.
SC Media+2ITU+2
-
More than
552 million identities (personal
records) were exposed in 2013.
ITU+2APN
News+2
-
Eight
“mega‑breaches” occurred (each exposing
10 million+ identities) in 2013, compared with
only one in 2012.
APN News+2ITU+2
-
According to
Kaspersky Lab statistics:
-
Their
products detected and neutralized ~5,188,740,554
cyber‑attacks on user computers and mobile
devices in 2013.
Securelist
-
Of those,
~1,700,870,654 attacks were launched from online
resources around the world.
Securelist
-
According to
the Open Security Foundation and Risk Based Security
analysis:
2014
-
According to
Gemalto’s Breach Level Index, more than
1,500
data‑breaches worldwide in 2014 led to
over
1 billion compromised personal data records.
TechCabal+3Thales
Group+3CNBC+3
-
The Identity
Theft Resource Center (ITRC) reported
783 data
breach incidents in the U.S. in 2014 — a
27.5% increase over 2013.
securitymagazine.com+2CBS
News+2
-
According to the
PricewaterhouseCoopers (PwC) “Global State of
Information Security Survey 2015”, there were ~42.8 million
security incidents detected worldwide in
2014 — up 48% from 2013 (an average of ~117,339 per
day).
Journal of Accountancy
-
One report
noted that for the first half of 2014, more than
375 million customer records were stolen or
lost in 559 known breaches worldwide.
Corporate Compliance Insights+1
-
A 23% increase
in data breaches was reported by Symantec
Corporation in 2014 compared to 2013.
2015
-
According to
Gemalto’s Breach
Level Index (BLI):
-
For the first
half of 2015, Gemalto reported:
-
According to
Symantec and other reports:
2016
-
According to the
Gemalto Breach Level Index, there were
1,792 data
breaches globally in 2016, which resulted
in nearly
1.4 billion compromised data records.
Thales Group+3GlobeNewswire+3Help
Net Security+3
-
According to the
Risk Based Security Data Breach QuickView report,
there were
4,149 breaches reported in 2016, which
exposed over
4.2 billion records worldwide.
Dark Reading+2SecurityWeek+2
-
In the first half
of 2016 alone: there were about
974 breaches
which exposed around
554 million
records.
2017
-
According to the
Gemalto Breach Level Index, there were approximately
2.6 billion
data records stolen, lost or exposed worldwide in
2017 — an 88 % increase from the prior year.
GlobalDots+2Thales
Group+2
-
The same dataset
reports about
1,765
publicly‑disclosed data breach incidents in
2017.
Thales Group+1
-
According to the
Risk Based Security data: there were ~5,207
breach events globally in 2017, which
exposed around
7.8 billion
records (based on one vendor’s
compilation).
Dark Reading+1
-
It was observed
that although the
number of
breach incidents did not rise dramatically (or even
declined slightly according to some sources), the
volume of
records exposed surged significantly. For
example, human error (mis‑configured systems,
accidental exposure) accounted for 1.9 billion of
the records compromised.
2018
-
In the first half
of 2018, there were
≈ 944
publicly‑disclosed data breaches worldwide,
which resulted in around
3.3 billion
data records being compromised (lost,
stolen, or exposed).
Thales Group+2Business
Today+2
-
Some sources
report that the same period’s figure is higher —
e.g., ~945 data breaches with ~4.5 billion records
compromised.
Help Net Security+1
-
The data show
that while the
number of
breach events did not necessarily increase
significantly compared to earlier years, the
magnitude
(records per breach) climbed sharply, indicating
that fewer but much larger successful attacks took
place.
Thales Group
-
The breakdown:
major social‑media platform breaches (including
Facebook/Cambridge Analytica) plus large‑scale
exposures in identity/theft vectors contributed a
majority of the records compromised.
2019
-
There were
7,098
reported breaches worldwide in 2019,
according to one major compilation.
securitymagazine.com+1
-
These reported
breaches exposed
over 15.1 billion records globally in
2019—a ~284 % increase compared to 2018.
SecurityWeek+1
-
By the first nine
months of 2019,
5,183
breaches had exposed
≈ 7.9 billion records.
Help Net Security
-
In the first half
of the year alone (~3,800 breaches) the number of
exposed records was about
4.1 billion.
2020
-
According to one
review, the number of publicly reported data
breaches in 2020 exceeded
1,900
incidents, of which many (≈ 49 %) lacked confirmed
numbers of records exposed. The total number of
records compromised in those breaches is reported to
have exceeded
37 billion,
a ~141% increase compared to 2019.
Governing+2GovTech+2
-
In the first
three quarters of 2020 alone, ~2,953
publicly disclosed breaches had been reported, with
~36 billion
records exposed by end of Q3.
GovTech+2CISO
MAG | Cyber Security Magazine+2
-
Ransomware‑related
breaches surged: one source reported
676 breaches
in 2020 that included a ransomware element — roughly
double compared to 2019.
Governing+1
-
A cybersecurity
statistics summary estimates that ransomware cost
businesses about
US$ 20 billion in 2020, and that there were
“nearly 550,000 cyber attacks per day” involving
ransomware.
2021
According to one
source, there were about
227.5 million
cyber-incidents globally in 2021 alone (from a
“2020-2025” attack-volume table).
Total Assure+2Statista+2
Another source states
“over 2,200 cyber-attacks occur daily” in 2025 (~800,000
per year) and mentions that 33 billion accounts will
have been breached in 2023.
DemandSage+2nationalcybersecurity.com+2
Some industry
commentary: “Over the last 21 years from 2001 to 2021 …
cybercrime has claimed at least 6.5 million victims …”
2022
-
According to the
Identity Theft Resource Center (ITRC) 2022 Breach
Report:
-
There were
817
total data compromises in 2022
(including breaches, exposures, etc.).
ITRC
-
Out of those,
802 were data breach events, with
46,209,107 victims impacted.
ITRC
-
According to the
Spirion 2022 breach summary:
-
1,595
incidents related to cyberattacks (rather than
human error or physical theft) compromised
374,992,920 individual records.
ISE Connects
-
From healthcare
sector data:
-
In the U.S.,
588 healthcare‑related breaches reported to the
U.S. Department of Health & Human Services (HHS)
Office of Civil Rights in 2022 affected
44,665,819 patient records.
DataBreaches.Net+2Lumifi
Cybersecurity+2
-
Global
breach‑level summaries suggest:
2023
-
A report by
Flashpoint states that in 2023 there were
approximately
6,077
publicly reported data‑breach incidents,
with over
17 billion personal records exposed
globally.
sos-vo.org+2Infosecurity
Magazine+2
-
According to
SpyCloud’s 2024 Identity Exposure Report:
researchers recaptured ~43.7 billion distinct
identity assets in 2023 (including ~32 billion
personally identifiable records) and found that
about 61% of
data breaches in 2023 were
infostealer‑malware
related.
SpyCloud+1
-
In the
healthcare sector of the U.S., more than
116 million
patient records were exposed across 655
breaches in 2023 — a marked increase from previous
years.
Cybersecurity Dive
-
In December
2023 alone: 1,351 publicly disclosed security
incidents and ~2.24 billion records breached.
2024
According to Statista,
there were over
15 million cyber-crime incidents worldwide in
2024.
Statista
One report estimates
about 239.6
million attack incidents globally in 2024.
Total Assure
For just ransomware-type
attacks: Cyber Threat Intelligence Integration Center (CTIIC)
reports about
5,243 known ransomware victims worldwide in
2024.
Corvus Insurance+1
2025 - to date
-
According to
Check Point Research, in Q1 2025 the average
organization experienced
1,925 cyber
attacks per week (a +47 % increase from
Q1 2024).
Check Point Blog
-
For Q2 2025 the
average surged to
1,984 weekly
attacks per organization globally, up ~21 %
year‑on‑year.
Check Point Blog
-
A broad overview
by Total Assure estimates about
292.9 million cyber‑attack incidents for
2025 (across the year) up from ~239.6 million in
2024.
Total Assure
-
Other sources
predict that in 2025 around
289 million
ransom ware attempt events will occur
globally, and that ~88 % of organizations will have
experienced one or more cyber incidents.
|
| |
|
As the cyber security
landscape evolves, it is critical for research teams to anticipate where
attackers may focus their efforts next and make their organizations more
resilient. The SecureIT4u Enigma 2.0
stops the Tried and True tactics along with any future attack techniques.
(Quantum / AI Cyber Attacks). |
|
Protect your
Organization from the New Generation of Threats
To secure your organization
from constantly evolving and advancing cyber attacks, you need a platform that
delivers comprehensive “zero” trust cyber threat protection at the speed and
scale of the Cloud while not being on the Cloud.
-
Stop threats before
they become attacks
-
Eliminate point
products and complexity
-
Prevent lateral
threat movement
-
See and prioritize
your biggest risks
|
|
The Problem
VPN- and firewall-centric
approaches can no longer protect against cyber attacks. Given enough time and
resources a hacker will always get in when software and passwords are utilized.
Enterprises worldwide are
investing billions in physical and virtual hardware to defend against evolving
threats and ransom ware attacks, but breaches are still on the rise.
The problem is simple;
users and applications are distributed, so traditional data center-based tools
such as VPN’s and firewalls no longer make sense.
-
86% of threats hide
in encrypted traffic that firewalls can’t inspect at scale
-
56% of enterprises
were targeted by a VPN-related cyber attack in 2023
-
400% more IoT/OT
attacks occurred in the last year
(IoT
security focuses on protecting connected devices and their data, while OT
security safeguards systems controlling physical industrial processes) |
| |
|
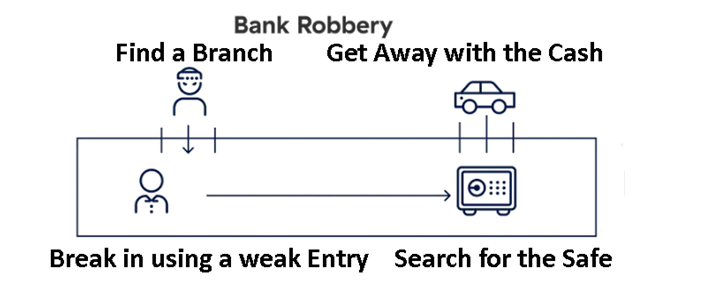
A Cyberattack is like a
Bank Robbery

 |
-
Attackers find you
-
Discoverable IPs are vulnerable—even firewalls and VPNs, which are meant
to protect you in the first place.
|
-
They compromise
you - Attackers
exploit vulnerabilities to establish a beachhead in your Network.
|
-
They move
laterally - Once a
machine is infected, the entire network is compromised.
|
-
They steal your
data - Sensitive
data across applications, servers, and entire networks is lost.
|
|
|
| Solution |
|
The SecureIT4u Enigma 2.0
100% combats every step in the attack chain. |
| Our approach eliminates the
attack surface, prevent compromise, eliminate lateral movement, and stop data
loss. |
|
|
HOME |
THE
ENIGMA 2.0 |
ABOUT |
CONTACT |
FUNCTIONALITY |
CYBER HISTORY |
WHY THE ENIGMA 2.0 |
|
Secureit4u USA LLC |
|
300 N. Center Street, Unit Six |
|
Casper, Wyoming
, USA 82061 |
|